Why choose our managed cyber security?
Is your business resilient against cyber attacks?
If your organisation relies on set and forget software to defend against cyber security threats, you may be leaving critical gaps in your defence. Effective security requires active oversight. Who is managing your alerts, patching your vulnerabilities, and responding to potential breaches in real-time?

Why choose managed cyber security?
At DLM IT, we act as your dedicated security partner. We don’t just install software; we provide comprehensive managed detection and response (MDR). Our team of security experts monitor your environment 24/7, ensuring robust protection against ransomware, data breaches, and unauthorised access.
Key Benefits:
- Proactive Threat Hunting: We find threats before they damage your business.
- 24/7 Security Operations: Round-the-clock monitoring by expert analysts.
- Reduced Complexity: A single trusted partner for all your security needs.
- Regulatory Compliance: Assistance with ISO 27001, GDPR, and ACSC Essential 8.
Our comprehensive cyber security solutions
We specialise in delivering integrated support and advanced security capabilities. As a leading Managed Security Service Provider (MSSP), we utilise industry-leading products to fortify your business.

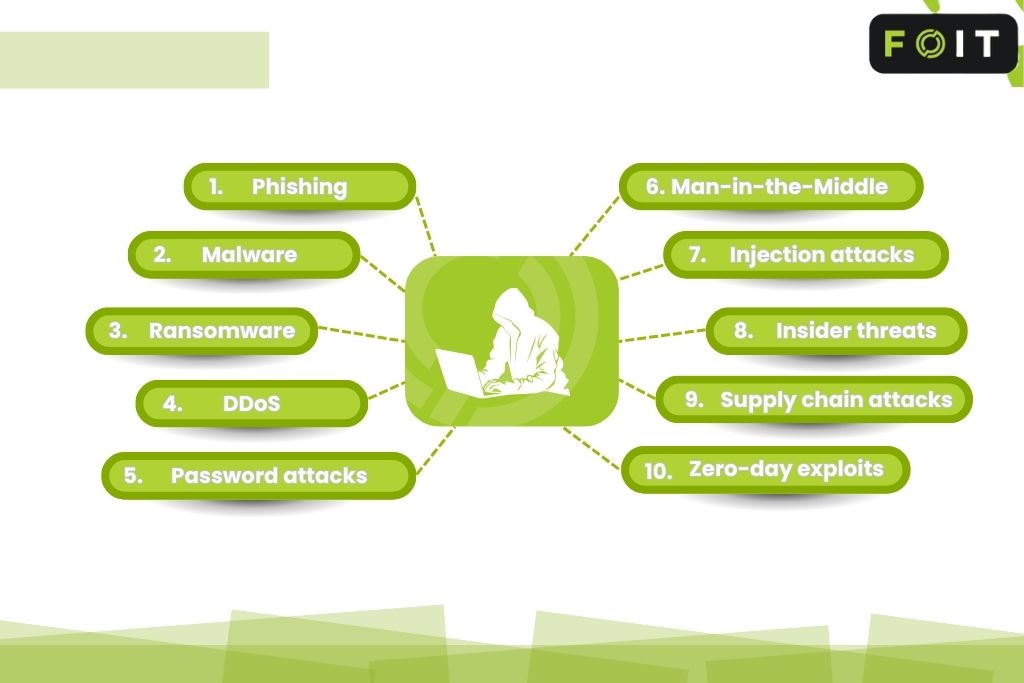
Defending against cyber security threats
We move beyond simple definitions to provide active defence against the most dangerous threats facing Australian businesses today.
- Advanced malware defence: From spyware to Trojans, our multi-layered security stack identifies and quarantines malicious software instantly.
- Ransomware protection: We implement robust backup strategies and immutable storage to ensure you never have to pay a ransom. Our EDR solutions block encryption processes before they lock your files.
- Phishing & social engineering: We utilise advanced email filtering and AI-driven threat intelligence to block deceptive emails that aim to steal credentials or financial data.
- DDoS mitigation: We safeguard your uptime with resilient network infrastructure and traffic monitoring that absorbs and deflects Distributed Denial of Service attacks.

 DLM IT has been an invaluable partner for our business. As our MSP, they've consistently delivered top-notch IT solutions. Their strategic approach to technology management has not only improved our operational efficiency but also ensured the security of our sensitive data. I highly recommend DLM IT for their professionalism and dedication to client success.”
DLM IT has been an invaluable partner for our business. As our MSP, they've consistently delivered top-notch IT solutions. Their strategic approach to technology management has not only improved our operational efficiency but also ensured the security of our sensitive data. I highly recommend DLM IT for their professionalism and dedication to client success.”

Achieve compliance: ACSC Essential Eight & NIST.
The Australian Cyber Security Centre (ACSC) recommends the Essential Eight strategies to mitigate cyber security incidents. We help you achieve maturity across all eight pillars:
- Application Control: Prevent execution of unapproved/malicious programs.
- Patch Applications: Remediate known vulnerabilities promptly.
- Configure Microsoft Office Macros: Block untrusted macros.
- User Application Hardening: Block web browser Flash, Java, and ads.
- Restrict Administrative Privileges: Limit access to systems.
- Patch Operating Systems: Keep OS versions up to date.
- Multi-Factor Authentication (MFA): Secure remote access and sensitive data.
- Regular Backups: Ensure data recovery capabilities.
By diligently implementing and aligning these strategies with your business’s unique risk profile and specific requirements, you can significantly fortify your readiness to confront cyber threats, both in the present and as they evolve in the future. We can help you become Essential 8 compliant with cyber security solutions aligned to the Essential 8 maturity levels
Enhance your cyber security standing with our comprehensive NIST-based approach
If you're seeking to bolster your business's cyber security posture, enabling seamless remote work from any device and location, our solutions are here to empower you.

Let DLM IT help you manage and monitor your business with our Cyber Security Services
Frequently Asked Questions
TopWhat is managed cyber security, and why do businesses need it?
Managed cyber security involves outsourcing the monitoring and management of your security infrastructure to a specialised provider like DLM IT. It ensures continuous, 24/7 protection against evolving cyber threats without the cost of building an in-house Security Operations Centre (SOC).
How does managed cyber security differ from traditional cyber security solutions?
Traditional cyber security solutions often require in-house management and reactive monitoring. Managed cyber security, on the other hand, involves external cyber experts who handle the day-to-day security operations, proactive threat detection, and incident response, allowing businesses to outsource complex security management and focus on core activities while benefiting from specialised security capabilities and resilience.
Is managed cyber security suitable for small businesses (SMBs)?
Absolutely. SMBs are frequently targeted because they often lack enterprise-grade defences. Our managed services are scalable, allowing you to access enterprise-level protection and expertise at a predictable monthly cost suitable for your budget.
How can managed cyber security help with compliance and regulatory requirements?
Managed cyber security providers are often well-versed in industry-specific compliance obligations and can assist businesses in implementing the necessary security controls and risk management strategies. We help you conduct audits, maintain data privacy, and achieve alignment with frameworks like the ACSC Essential Eight.. This support helps businesses avoid legal issues and financial penalties while strengthening their overall security posture.
Can you help with cyber insurance requirements?
Yes. Many insurers now require specific controls like MFA, EDR, and offsite backups. We assist you in implementing these controls to ensure you are eligible for coverage and compliant with policy requirements.