Data leaks cost companies millions each year. One wrong email, weak password, or misplaced file can expose thousands of records.
Data Leak Protection (DLP) is the safeguard that prevents this. It monitors and blocks sensitive information before it slips out of your system.
What is a data leak?
A data leak happens when sensitive data is exposed without permission. Unlike a data breach, which often comes from an outside attack, a leak can occur quietly through human error, insider misuse, or weak security controls.
This matters because even a small leak can have major consequences. Organisations risk financial loss, compliance fines, and lasting damage to their reputation. Worse, the loss or theft of critical data, such as customer records, financial data, or confidential information, can erode trust and create long-term harm.
Types of data: leak, loss, and breach
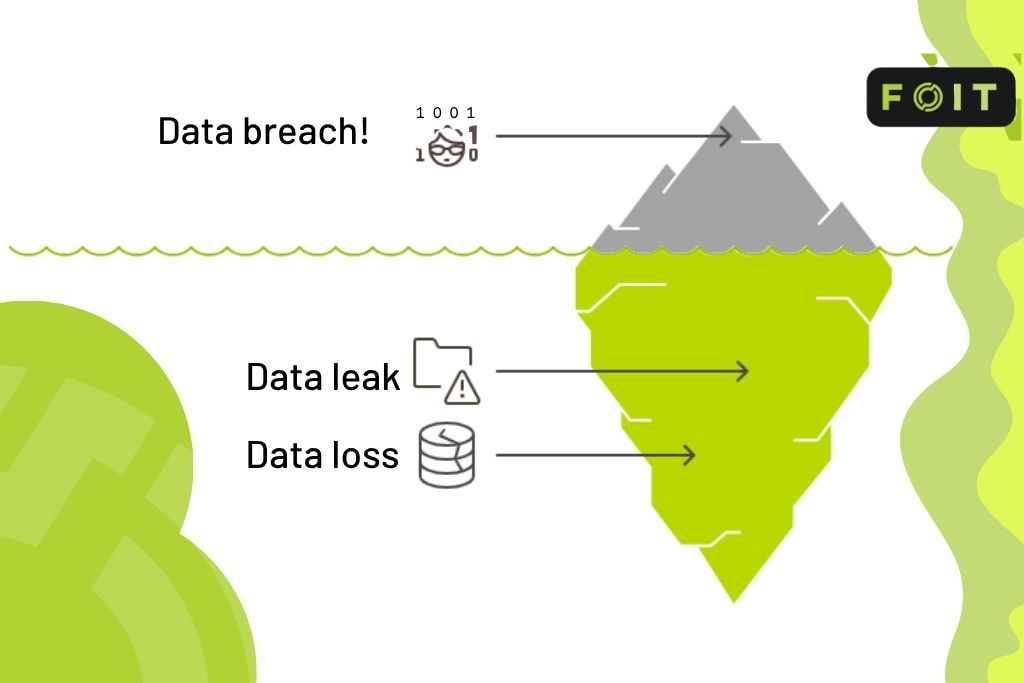
Data leak
The unauthorised exposure of sensitive information, usually caused by internal mistakes, misconfigurations, or weak access controls. It often happens accidentally but can still lead to serious consequences.
Data loss
The permanent loss of data due to deletion, corruption, hardware failure, or human error. This typically means the data is no longer retrievable and may affect operations or compliance.
Data breach
A deliberate act where someone gains unauthorised access to data, often through hacking, malware, or other cyberattacks. Breaches are criminal in nature and usually result in large-scale exposure or theft.
Understanding these differences helps organisations apply the right protection strategies. While DLP is primarily designed to prevent data leaks, it also plays a supporting role in protecting against loss and detecting early signs of a breach.
What is data leak protection (DLP)?

Data Leak Protection (DLP) is a cybersecurity solution designed to prevent sensitive information from leaving your organisation without authorisation.
DLP systems monitor the movement of data across your network, devices, emails, and cloud platforms. They automatically detect confidential information, enforce security policies, and block risky behaviours, such as copying files to a USB drive or sending client data through personal email accounts. These systems also alert your security team when suspicious activity occurs.
Why data leak protection is important
Australian organisations are under increasing pressure to protect sensitive data as cyber threats grow and privacy regulations tighten. According to the Office of the Australian Information Commissioner (OAIC), data breaches reported under the Notifiable Data Breaches scheme rose by 19% in the first half of 2023 alone.
A single leak can lead to legal penalties, financial loss, and lasting reputational damage. Strong data leak protection supports organisations in four important ways:
- Compliance and Regulations. Meeting compliance standards is a key reason to invest in data leak protection. Frameworks such as GDPR, HIPAA, and the Payment Card Industry Data Security Standard (PCI DSS) require strict controls. Without them, a data leak or data breach can bring heavy fines and legal trouble.
- Business Risk. A data leak can quickly result in a data breach, putting revenue and stability at risk. Beyond direct financial loss, leaks can trigger customer churn and expose critical data. In many cases, recovery costs far outweigh the cost of prevention.
- Stronger Security Posture. Leak prevention is a cybersecurity practice that strengthens overall defence. With the right DLP tools and prevention strategies, organisations protect their data, reduce the risk of unauthorised access, and maintain control of information at every stage.
How data leak prevention (DLP) works
Finding and protecting data
DLP finds sensitive data through data identification and data classification. It monitors data at rest, data in motion, and data in use. With data encryption and access controls, it reduces leaks.
Example: encrypting customer records so even if stolen, they can’t be read.
Tools that keep data safe
DLP solutions work in different areas: endpoint DLP protects devices, network DLP monitors traffic, and cloud DLP secures online storage. They use real-time monitoring to prevent data loss.
Example: stopping a file with financial data from being uploaded to an unknown cloud account.
Techniques DLP uses to stop leaks
DLP software relies on several techniques to prevent exposure:
- Pattern matching – scans text for things like credit card numbers.
- Fingerprinting – identifies exact files or documents to stop leaks.
- Machine learning – detects unusual behaviour that could signal a data breach.
- Blocking actions – stops sensitive data from leaving the organisation by email, chat, or cloud uploads.
- Access controls – ensures staff have access only to the data they need.
Types of DLP solutions
Not all DLP systems are the same. Each solution covers different areas of your IT environment. There are three main types of DLP used in businesses. Each focuses on a different layer of data protection.
Endpoint DLP
Endpoint DLP secures data on individual devices, such as laptops, desktops, or USB drives. It monitors actions like copying, printing, or transferring files. If a risky behaviour is detected, it can block the action or alert your team.
This is critical for remote work setups and mobile employees.
Network DLP
Network DLP protects data as it moves across your organisation’s systems. It monitors internal emails, internet uploads, file transfers, and messaging platforms. When sensitive data tries to leave the network, the DLP tool can stop it in real time.
This layer is key for detecting external leaks and unauthorised sharing.
Cloud DLP
Cloud DLP protects data stored in or shared through cloud services like Microsoft 365, Google Workspace, or Dropbox. It keeps cloud-based files secure and applies policies across users and apps.
As more businesses move to the cloud, this DLP type has become essential.
What are DLP best practices?
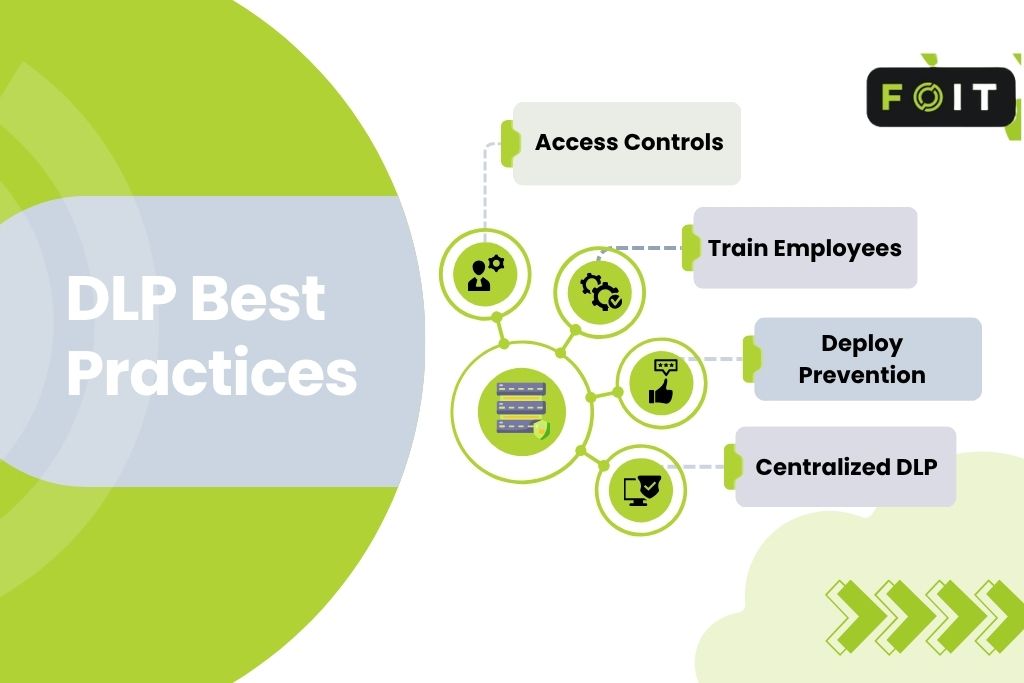
Effective data leak prevention (DLP) comes from combining technology with smart policies. These best practices help organisations protect sensitive data and reduce the risk of a data leak or data breach.
- Limit access to data. Give staff access only to the data they need for their role. This reduces insider misuse and keeps critical data secure.
- Train employees. Run regular security awareness training so employees understand how accidental data leaks occur and how to prevent them. Human error is one of the most common causes of data leaks.
- Deploy prevention systems. Use prevention systems and automated prevention tools to detect risks early. These systems block unauthorised access and data exposure, reducing the chance of a serious incident.
- Centralise DLP policies. Keep DLP policies under one security team. Central control ensures consistent rules, quick responses, and clear accountability across the organisation.
Frequently Asked Questions (FAQ)
How do I report a data leak?
Data leaks occur when sensitive data is exposed by mistake, insider misuse, or cyberattacks. Weak controls, poor access management, and missing data encryption also cause leaks, which can quickly result in a data breach if exploited.
What is the difference between a data leak and a data breach?
A data leak is the unauthorised exposure of data, often caused by mistakes, insider misuse, or weak controls. A data breach usually involves an external attack where criminals steal or access information illegally.
What does DLP stand for?
DLP stands for Data Leak Prevention or Data Loss Prevention. Both terms describe systems, tools, and policies that protect sensitive data from leaks, misuse, or theft.










