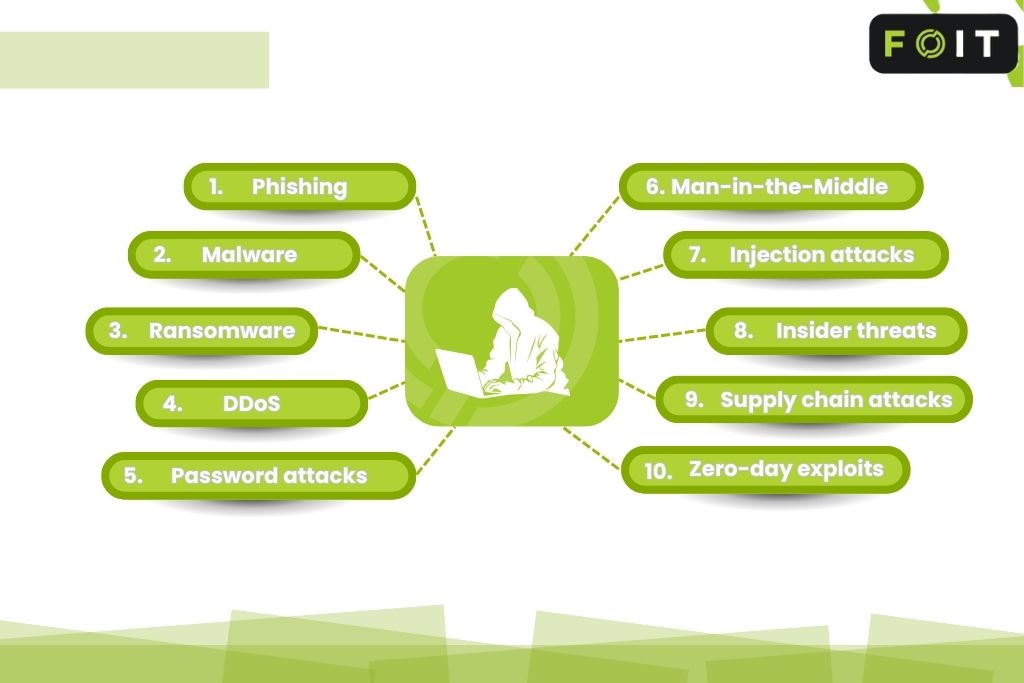
Ransomware Protection Guide: Complete Security Strategy
Ransomware protection is critical for Australian organisations. Attacks hit councils, healthcare, schools and businesses, causing weeks of downtime and data loss. If you rely on digital systems, you need a clear ransomware prevention and recovery plan before attackers strike. This guide shows you how attacks work, the local threat, and specific steps to protect your…
Read more
26 January 2026